Introduction
When external threats dominate headlines, many businesses assume the biggest risk lies outside their walls. But internal compromise from careless mistakes or deliberate misuse and is a far more invisible and insidious threat. The worst part? Compliance frameworks like GDPR, SOC 2, ISO/IEC 27001, NIST 800‑53, HIPAA, and PCI‑DSS v4.x all require rigorous controls for detecting, logging, and responding to insider activity. Most organizations simply aren’t equipped.
In this post, we’ll unpack why insider threats matter under each framework, explain where organizations typically fall short, and show how EXIGENCY‘s on‑prem infrastructure ensures compliance and protects your organization from within.
GDPR & ISO/IEC 27001: Protecting Personal Data from Internal Misuse
Under GDPR, personal data must remain secure at all times and even from those within your organization. Violations can incur fines up to 4 % of global annual turnover. ISO/IEC 27001 calls for continuous user access review, incident response policies, and proactive monitoring to ensure internal access aligns with least privilege principles.
Combined, these frameworks demand encryption, strict access control, and the ability to trace who accessed what, when, and why; within an integrated audit trail.
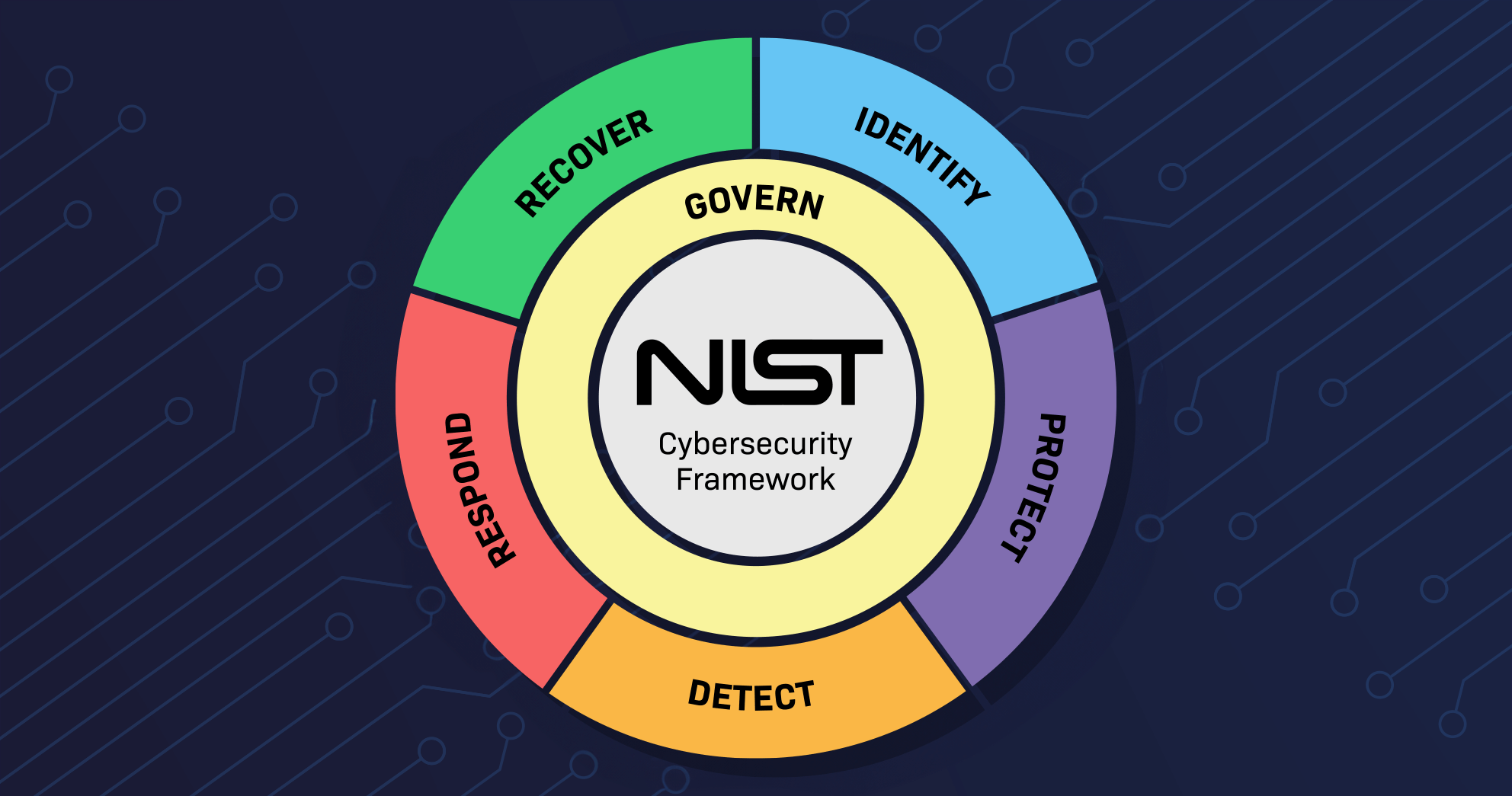
SOC 2 & NIST 800 53: Monitoring for Compliance and Control
SOC 2 Trust Services Criteria mandate system activity monitoring, data access reviews, and prompt detection of anomalous behavior. Without this, auditors will flag your security monitoring as insufficient. Similarly, NIST 800‑53 specifies control families such as AU (Audit) and AC (Access Control) that require full logging of insider activity, alert thresholds, and incident response procedures.
Together, these frameworks create a layered expectation: you must detect, alert, and respond to internal anomalies in real time.
HIPAA & PCI DSS v4.x: Defending Regulated Data from Within
HIPAA requires organizations to implement audit controls and log mechanisms to record access and activity to protected health information (PHI). You must be able to trace unauthorized attempts and even if they originate internally. PCI‑DSS v4.x mandates daily log monitoring, restricted access to cardholder data environments, and defined procedures to handle violations by internal users.
These regulations leave no room for undocumented access or unidentified internal misuse. They require defensible systems that log and alert on every attempt to access sensitive data.
Common Gaps in Insider Threat Detection
Even compliant organizations fall short in several areas:
- Insufficient access reviews: Accounts remain active long after role changes or terminations
- Lack of real-time monitoring: Many rely on batch reviews, missing critical indicators
- Weak segmentation: Once inside the environment, malicious insiders can pivot across systems
- Relying on cloud logging: Logs can be delayed, incomplete, or unavailable during incidents
These gaps make detection reactive instead of proactive and if an incident happens, the compliance fallout can be severe.
EXIGENCY’s Infrastructure: Compliance-Ready and Insider-Resistant
EXIGENCY addresses insider risk through hardened on-prem architecture:
- Segmented VLANs and role-based access ensure least-privilege policies are enforced
- Centralized SIEM and audit logging (ICS01/ICS02) capture all user activity with immutable timestamping
- Automated alert triggers for log-on anomalies, unauthorized file access, or unauthorized privilege changes
- User access reviews and role termination workflows integrated into Active Directory and RADIUS logs
- Encrypted data partitions and restrictions on PHI/cardholder zones to isolate sensitive workloads
This infrastructure is designed from the ground up to comply with all six frameworks, ensuring any breach, change, or anomaly is visible and auditable.
FINAL THOUGHTS: See It Before It Happens
Insider threats aren’t just cyber risk but they’re compliance risk. From GDPR to PCI‑DSS, every major standard demand controls that identify, log, and respond to internal misuse. EXIGENCY’s on-prem solutions do more than just meet those requirements but they bake them into daily operations. You get full visibility, direct control, and an audit-ready environment at all times.
Don’t wait for a compliance audit or internal incident to realize your vulnerability. Become invisible to insider threat all while staying fully visible to auditors. Choose EXIGENCY and reclaim control from the inside out.



No comment