Introduction
Businesses are under siege. From phishing and ransomware to insider threats and advanced persistent attacks, the digital landscape is brutal. The most damaging part? Most businesses don’t even realize their weaknesses until it’s too late. This is why frameworks like the NIST Cybersecurity Framework (CSF) are not optional; they are foundational. Developed by the National Institute of Standards and Technology, the NIST framework is the gold standard in establishing cybersecurity hygiene. But most businesses either misunderstand it or assume it’s only for government contractors. The truth? If you’re not using it, you’re gambling with your data, compliance, and reputation.
This blog post unpacks the NIST CSF in plain English; explains why it’s crucial for IT leaders, CISOs, and MSPs; and shows how EXIGENCY integrates it into every hardened on-premise infrastructure deployment.
What Is the NIST Cybersecurity Framework?
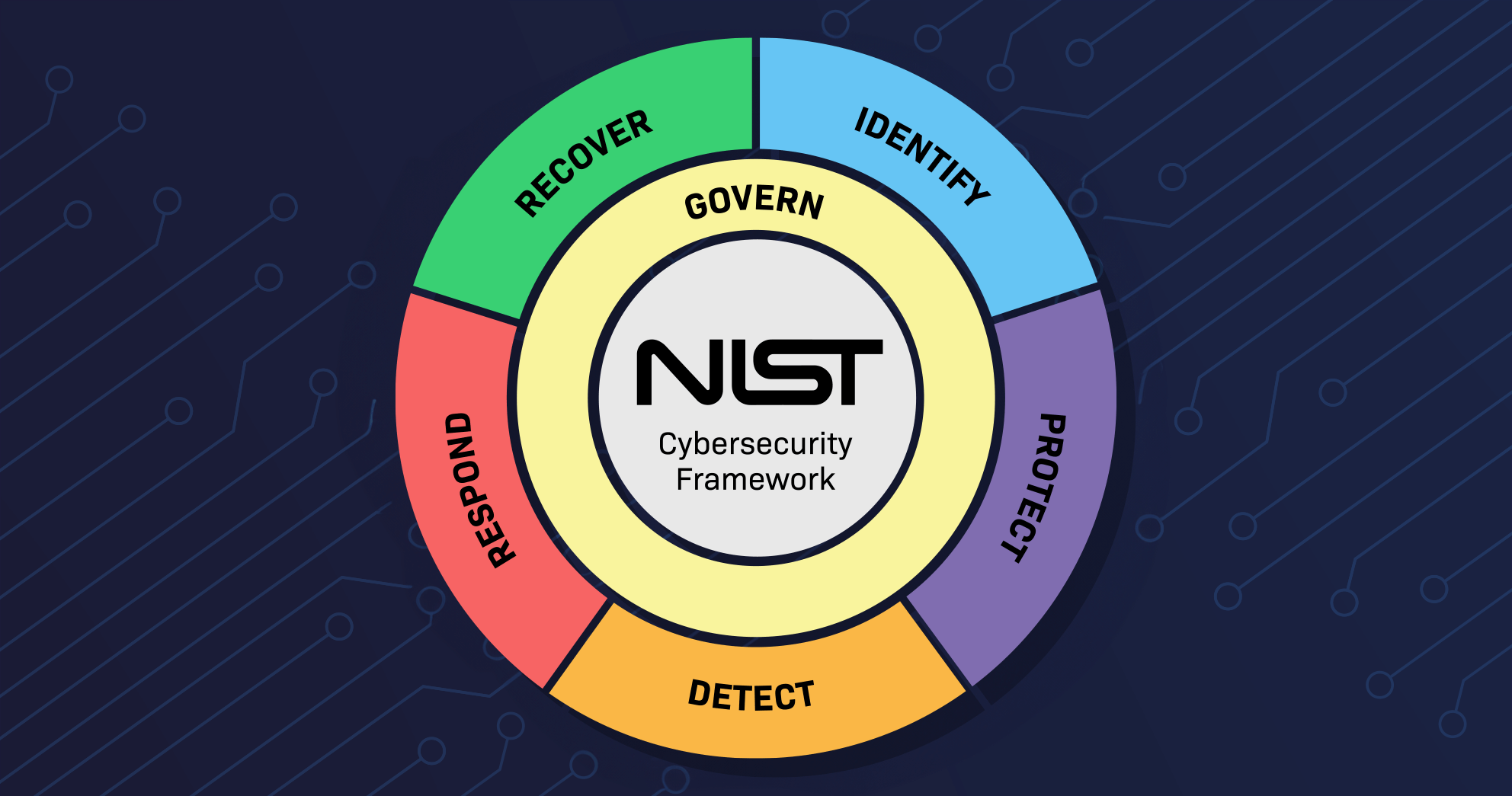
The NIST Cybersecurity Framework was created in 2014 in response to a presidential executive order. It’s a voluntary framework, yet it’s now de facto mandatory for any business serious about security. At its core, NIST provides a structured way to identify, protect, detect, respond, and recover from cyber threats. These five pillars are known as the Framework Core, and they guide businesses of all sizes through the complex task of securing their digital infrastructure.
It’s not just a checklist; it’s a living system of policies, practices, and controls. From technical safeguards like multi-factor authentication to risk analysis and incident response, NIST maps out how to operationalize cybersecurity across your entire organization.
Who Needs to Comply With NIST?
You might think, “We’re not a federal agency, so this doesn’t apply.” False. Increasingly, vendors, contractors, healthcare providers, and financial institutions are being required to adhere to NIST standards. Either through direct regulation or contractual obligations. HIPAA? It maps directly to NIST. PCI-DSS? Overlaps with NIST. SOC 2? Strong parallels. Many companies unknowingly duplicate efforts across multiple standards when aligning to NIST would streamline their compliance.
For EXIGENCY clients, we implement NIST-aligned controls from the ground up, whether you’re a law firm storing sensitive client data, a clinic managing electronic health records, or an eCommerce brand processing payment.
Breaking Down the 5 Core Functions
Each function of the NIST framework serves a purpose:
- Identify: Know what systems, data, and users exist. You can’t protect what you don’t understand.
- Protect: Apply technical and physical safeguards; firewalls, encryption, training, access controls.
- Detect: Use logging, SIEM, monitoring tools to catch threats early.
- Respond: Establish incident response protocols; who does what, when, and how.
- Recover: Create backups, business continuity plans, and restoration procedures.
These functions break into 23 categories and over 100 subcategories. That might sound overwhelming, but that’s where EXIGENCY steps in; we handle the entire translation from policy to deployment.
Benefits Beyond Compliance
Businesses that embrace NIST do more than check boxes, they build resilience.
- They bounce back faster after attacks
- They reduce liability in lawsuits or breach disclosures
- They gain trust with clients and partners
- They maintain business continuity even during incidents
Moreover, aligning with NIST is a competitive differentiator. Clients, investors, and auditors look for companies who can articulate their security stance. With NIST, you’re not just compliant, you’re future-ready.
why EXIGENCY Builds NIST Into Every Deployment
EXIGENCY specializes in self-hosted, on-premise IT environments. Why? Because cloud platforms don’t give you full control. When building these environments, we apply NIST at every level:
- Firewalled and segmented VLAN architecture
- Zero-port tunneling for private remote access
- Centralized identity access management (ADDS, RADIUS, SSO)
- Redundant, geo-separated encrypted backups
- Privileged access logging and SIEM alerts
We also help clients build System Security Plans (SSPs), perform risk assessments, and document control matrices based on NIST. Our infrastructure is designed not just to run but to endure cyber threats.
FINAL THOUGHTS: SECURE BY DESIGN, NOT BY HOPE
Cybersecurity isn’t a product; it’s a strategy. The NIST Cybersecurity Framework gives businesses a practical path to reduce risks, document policies, and ensure operational continuity. Too often, organizations fall into the trap of buying tools instead of building strategy. NIST fixes that. It focuses on outcomes, not buzzwords.
Partnering with EXIGENCY means you’re not starting from scratch. We embed NIST into your network, systems, and daily operations so you’re never left exposed.



No comment